Update: The Full version of NIST 800-82 Rev 3 has been released.
The National Institute of Standards and Technology (NIST) that is a part of the US Department of Commerce had invited public comments before release of the Revision 3 of the NIST 800-82 Guide to ICS Security, we had a blog post that talked about this a few months ago here.
This Initial public draft has now been released for review by stakeholders and is available to read and review. You can download the document from the link here. NIST 800-82 Rev 3 Guide to Operational Technology draft

Notice now the title is Operational Technology (OT) rather than just ICS (Industrial Control Systems).
What are ICS?
ICS are used in industries such as Oil & Gas production, Chemicals manufacturing, Pharmaceutical plants, Fossil Fuel Power Generation plants, Nuclear power plants , discrete parts manufacturing plants as well as government infrastructure such as city water supply and sewage treatment plants.
What do we mean by OT?
OT stands for Operational Technology. These systems are different than the IT systems that we see in banks or stock markets. The main job of these systems is not data processing but controlling physical systems.
For more information on difference between OT security and IT security please see this.
Compared to ICS however, OT encompasses even more systems than what are considered the domain of the traditional ICS and these include the following
- Dams and related water works
- Building Automation Systems
- Data Center HVAC (Heating, Ventilation and Air Conditioning systems)
- Food & Agriculture sector
- Healthcare including Hospital automation and medical devices
- Transportation (think Train Signaling Systems, Underground METRO station HVAC systems
and many more systems that are not just IT systems but known as cyber-physical systems i.e they control physical objects such as valves, gates, machinery, vehicles and so on.
Here is a typical Building Automation System architecture that is shown in the NIST 800-82 Rev 3 draft.
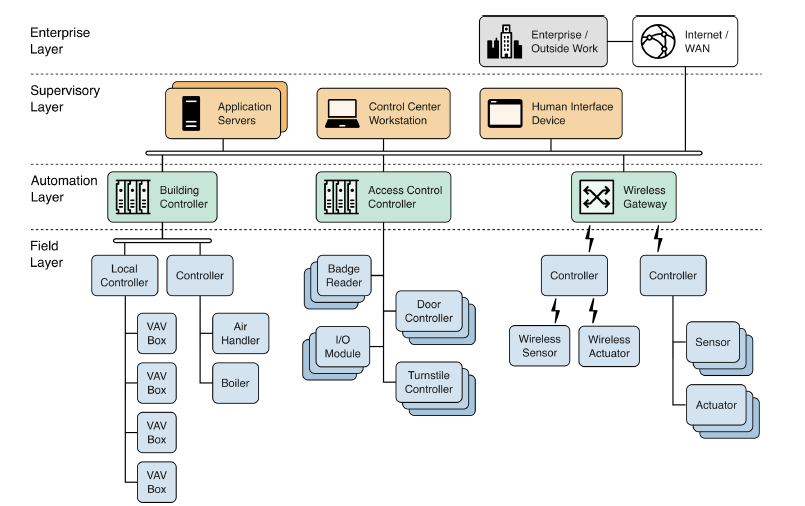
NIST recognizes that many OT systems have the same characteristics and issues as do Industrial Control Systems such as DCS, PLC, SCADA, SIS and similar and thus has expanded the scope of the guide to include all Operational Technology Systems.
Changes in 800-82 Rev 3 from 800-82 Rev 2
The highlights in this revised guide are:
- Expansion in scope from industrial control systems to operational technology (OT).
- Updates to OT threats and vulnerabilities.
- Updates to OT risk management, recommended practices, and architectures.
- Updates to current activities in OT security.
- Updates to security capabilities and tools for OT.
- Additional alignment with other OT security standards and guidelines, including the Cybersecurity Framework.
- New tailoring guidance for NIST SP 800-53 Revision 5 security controls
- An OT overlay for NIST SP 800-53 Revision 5 security controls that provides tailored security control baselines for low-, moderate-, and high-impact OT systems.
Here is part of the Executive Summary
This document provides guidance for establishing secure operational technology (OT)1 while addressing OT’s unique performance, reliability, and safety requirements. OT encompasses a broad range of programmable systems and devices that interact with the physical environment (or manage devices that interact with the physical environment). These systems and devices detect or cause a direct change through monitoring and/or control of devices, processes, and events. Examples include industrial control systems (ICS), building automation systems, transportation systems, physical access control systems, physical environment monitoring systems, and physical environment measurement systems. The document provides an overview of OT and typical system topologies, identifies typical threats and vulnerabilities for these systems, and recommends security countermeasures to mitigate the associated risks.
OT is critical to the operation of U.S. critical infrastructures, which are often highly interconnected, mutually dependent systems. It is important to note that while federal agencies operate many of the nation’s critical infrastructures, many others are privately owned and operated. Additionally, critical infrastructures are often referred to as a “system of systems” because of the interdependencies that exist between various industrial sectors as well as interconnections between business partners.
Initially, OT had little resemblance to traditional information technology (IT) systems in that OT systems were isolated, ran proprietary control protocols, and used specialized hardware and software. As OT are adopting IT solutions to promote corporate business systems connectivity and remote access capabilities, and being designed and implemented using industry-standard computers, operating systems (OSs), and network protocols, they are starting to resemble IT systems. This integration supports new IT capabilities, but it provides significantly less isolation for OT from the outside world than predecessor systems, creating a greater need to secure OT systems. The increasing use of wireless networking places OT implementations at greater risk from adversaries who are in relatively close physical proximity but do not have direct physical access to the equipment. While security solutions have been designed to deal with these issues in typical IT systems, special precautions must be taken when introducing these same solutions to OT environments. In some cases, new security solutions are needed that are tailored to the OT environment.
Where can I get more information?
You can download the NIST 800-82 Rev 3 draft from the link above and review it.
How do I learn more about Industrial Cybersecurity and OT Cybersecurity?
Simply take our Industrial Cybersecurity course. Learn everything about protecting Industrial systems and Operational Technology systems from cyber attacks.
When you take the Abhisam Industrial Cybersecurity course , you have the option to qualify as a CICP- Certified Industrial Cybersecurity Professional.



