ICS Cyber Security for Chemical plants- Introduction
Industrial Control Systems (ICS) are used in all modern chemical plants. These Industrial Control Systems play a crucial role in maintaining the efficiency, reliability, and safety of chemical plant operations. Currently the global chemical industry is facing challenging times related to energy costs, raw material costs and supply chain problems. The last thing it wants are additional risks of disruption due to cyber attacks. Let us now see how to reduce this risk by implementing cybersecurity in the chemical industry.
ICS in Chemical Plants
These systems encompass various types of control systems, including those that are based on different varieties of Distributed Control Systems (DCS) and Programmable Logic Controllers (PLC) systems which collectively manage and monitor industrial processes. Some chemical process plants may also use (or be interfaced with) SCADA (Supervisory Control and Data Acquisition Systems).
These systems are also referred to as OT Systems (OT stands for Operational Technology) to distinguish them from IT Systems. Note that IT systems process only data whereas OT Systems process data and also monitor and control physical objects and parameters.
What functions do ICS carry out in chemical plants?
These systems control the intricate processes involved in chemical production, from managing the flow and mix of chemicals, to monitoring parameters like temperature, pressure, level and density. The accuracy and precision of ICS are paramount in ensuring product quality, operational safety, and environmental compliance. Some of these systems are also used as Safety Instrumented Systems (SIS) that are used to protect plants from dangerous occurrences by appropriate alarms and trips.
ICS carry out various functions such as:
1. Basic Process Control : These systems monitor parameters and control the process based on set points configured by process engineers. They may also be used to control batch recipes. These ICS are also referred to as BPCS.
2. Process Optimization: Some ICS may also be used for optimization of production processes to increase yields and reduce energy costs.
3. Safety and Risk Management: Many chemical plants process hazardous, toxic and/ or explosive materials. In order to prevent dangerous occurrences, many chemical plants use special type of ICS which are known as Safety Instrumented Systems or SIS for short.
4. Control of specialized equipment: Many chemical plants use specialized equipment such as Gas Turbine power plants, fired heaters, furnaces, boilers, chillers, Nitrogen generation plants and so on. Different types of ICS are used to monitor and control these package units.
5. Data and Analysis: Specialized ICS such as Vibration Monitoring Systems for turbomachinery and compressors, provide real-time data, condition monitoring and allow these machines to be run safely.
Risks to Chemical Plants from Cyber threats
Many chemical plants today all over the world are an attractive target for all kinds of bad actors including state and non state actors for various reasons, but mainly due to the following reasons:
- A successful attack can result in an industrial disaster on a massive scale. For example the (failed) TRITON attack was carried out against a highly reliable Tripe Modular Redundant Safety Instrumented System (brand TRICONEX) that was meant to cause a disaster as it was used to keep several hazardous processes safe in a Saudi petrochemical manufacturing plant.
- Many ICS in chemical plants are not that well protected against cyber threats nor have they been risk assessed against cyber attacks.
- Cost of attacking is very less as compared to a conventional attack using missiles and drones that could be easily defended by the host country.More importantly it is difficult to attribute ICS Chemical plant cyber attacks to the perpetrators. In fact even some “unwanted incidents” in chemical plants due to unexpected or strange failures of equipment may be in reality due to cyber attacks (but not revealed as such by the victims even though they may know it).
What can be done to ensure ICS Cyber Security for chemical plants?
There are several steps that can be taken to prevent cyber attacks on chemical plants and if in spite of precautions an attack does take place, building defenses so that safety does not get affected.
1. OT Cybersecurity Awareness
This is the first step to be taken. Unless plant personnel are aware of the threats and implications, they cannot defend against them. You can take the Abhisam OT Cybersecurity Awareness training for your employees, contractors and other stakeholders who may be involved in designing, building, maintaining and operating your plant.

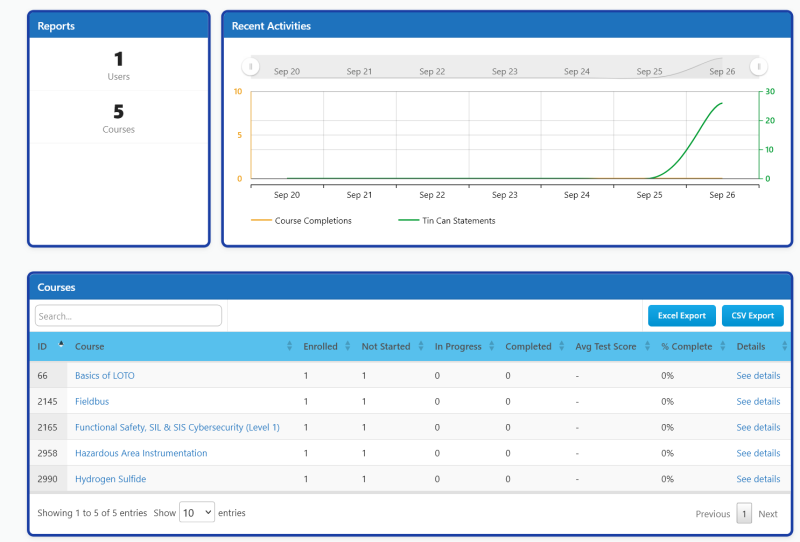
Your manager also gets a dashboard to view and track employees progress through the training as shown below in the sample view. This view includes progress for other Abhisam courses if required. This means that even if you do not have your own Learning Management System, you can get this functionality. Great for complying with training requirements, since all activity is automatically logged and stored. This means automatically you can have training records management.
2. Higher Level OT Cybersecurity Training for plant engineers and IT auditors
In parallel to the above you should train your plant engineers who are involved in design and or maintenance of the ICS to learn about Industrial Cybersecurity in detail. You should also train your IT security auditors in OT security as they will be critical to implementing. The best way to do this is by taking the Abhisam Certified Industrial Cybersecurity Professional course.

It is the only such course that fits in most budgets, as compared to other more expensive certifications.
3. Auditing Current Security posture
The current security posture of the ICS and/or other OT systems should be analyzed to find shortcomings that can then be addressed in the Security plan. You also need to carry out an ICS Security risk assessment
4. Security Plan
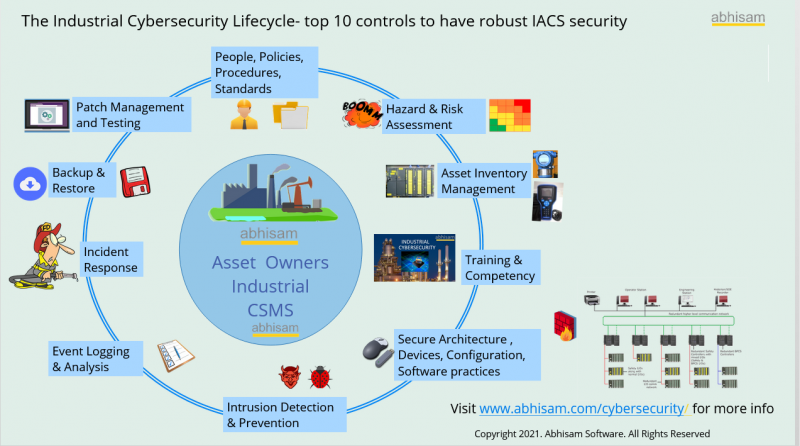
This is developed to plan in detail how OT cybersecurity can be implemented and maintained. It can make use of the Abhisam OT Cybersecurity Lifecycle that has 10 critical control points that if managed well will enhance your chemical plant’s security posture to a very high level.
ICS Cyber Security for Chemical Plants- Challenges
There are several challenges that are faced in implementing ICS Cyber security in chemical plants. Some of these are listed below:
1. Standards
There is no one standard that you can follow and be sure that your site is now secure. This is understandable since every ICS in a particular plant is an almost unique implementation of various devices and systems.
There are multiple standards, all of which are useful in their own way, so you need to decide which one to follow based on your unique configuration and under which regulatory area the plant is located.
For example, ANSI/ISA/ IEC 62443 is well suited for OT Cybersecurity in chemical plants; however it has several parts and many of those parts are still not published. You can make use of those parts that have been published and are relevant to your situation.
Similarly NIST 800-82 is now available as Revision 3 which covers most aspects of ICS Cyber Security for chemical plants.
Note that for Safety Instrumented Systems, you can follow IEC 61511 (ISA S84 in the US) which have some clauses related to SIS cyber security.
For specific guidance for Safety Instrumented Systems, you can follow the technical report ISA-TR84.00.09-2023 Cybersecurity related to the Functional Safety Lifecycle-Draft published
2. Legacy configuration practices that did not take ICS cyber security into consideration secure internet connectivity practices. You can find many of these on search engines like SHODAN.
3. IT OT Convergence
Many ICS are connected to higher level management systems such as ERP systems and other MIS or Production planning systems. This is popularly known as IT OT convergence which some companies actively promoted.
However , these system architectures may not follow cybersecurity best practices. Since these have been working for a long time, it is difficult to convince management to change them based on perceived threats. However, informed plant operations & engineering managers, as well as CISOs must take the lead and educate the top management on how these systems (IT and OT) should be configured to securely work with each other in a synergistic way with very little risk.
4. Cyber Risk Management and Process Safety related Risk Management
Currently both of these domains do not cover OT cybersecurity risks. Current cyber security risk management practice focuses on Information security and as far as Process Safety is concerned, it focuses on equipment failures, wrong operations due to deviations from SOP, human errors and such. It does not account for malicious intents. Thus OT cybersecurity falls between the cracks so to say and is nobody’s area.
Abhisam’s new upcoming Cyber PHA training course is a great way to understand how to carry out Process Safety risk assessments for malicious intent cyber attacks on DCS, PLC, SCADA or SIS. Note that many safety practitioners who carry out HAZOP or LOPA Studies do not consider the effects of cyber attacks that can degrade the BPCS or the SIS.

5. Industrial IoT devices
The sudden explosion of Industrial Internet of Things projects in chemical plants led to various architectures which are not necessarily according to the old Purdue model. They may bypass the normal DMZs that may have been installed for ICS and be not that secure. 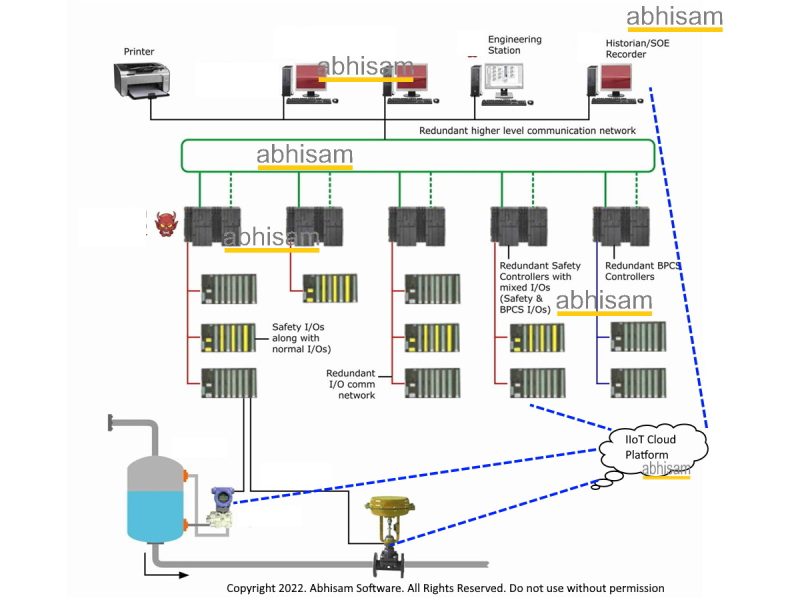
Know more about this here IEC 62443-4-3
FInal Takeaways
ICS Cyber security for chemical plants is essential and should be a focus area of all managements of such industries. There are challenges of course, but they are all solvable problems. Managements should be supportive of these initiatives, so that the risk of disasters from cyber attacks gets reduced considerably.
Current security postures of many chemical plants need to be improved a lot to protect them from the effects of a cyber attack. Furthermore many Process Safety Risk assessments such as HAZOP or LOPA do not consider the effects due to cyber attacks, this needs to change as otherwise many of the mitigations that depend on the Control System or Safety Instrumented System may not work.
For more information please contact us at sales@abhisam.com