Abhisam is pleased to announce that the Abhisam OT Cyber Security awareness training course will soon be available online. This OT security awareness etraining is a great way to train large numbers of your employees in the basics of OT Cyber Security/Industrial cyber security.
This course can be deployed globally via the Abhisam Learning Portal and managers or training administrators can view learner activity and progress via a training dashboard that shows details at a granular level. This is excellent for upgrading the competency of your employees, at a very low cost and rather quickly, as compared to other ways.
Since learner activities are recorded in the system automatically this creates an automated training records management system, that can be used to demonstrate training compliance. This can become your own OT Awareness Learning Management system that can upskill your employees.
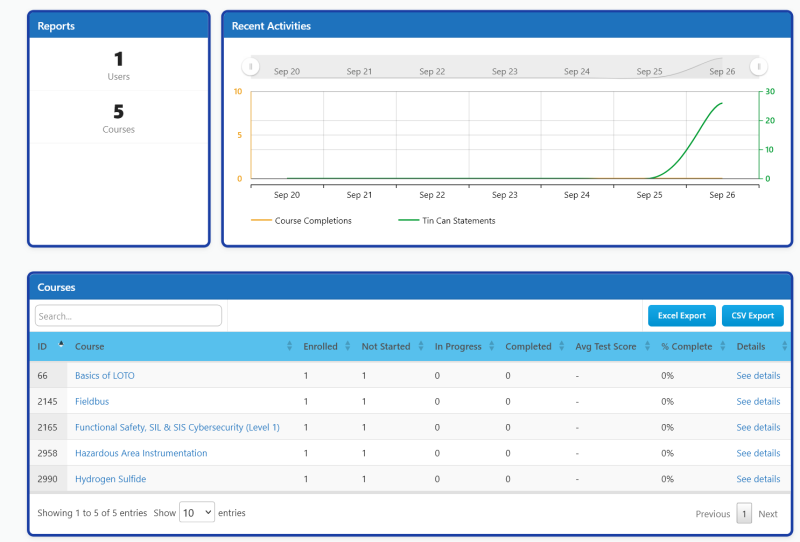
The below screen shot shows this being used for other courses in the Abhisam catalog, but can be used for the OT cyber security awareness training as well.
Why this OT Cyber Security awareness training course?
Cyber attacks on OT systems are growing. In fact today cyber attacks on OT systems have grown by 40% this year already, as compared to last year. Many OT systems are legacy systems and difficult to secure without investing a lot of time and money. It is better to have a very widespread OT security awareness training campaign that can be deployed across the organization. Workers and line supervisors, are generally not directly responsible for OT security, but could be unwitting victims who unknowingly enable a cyber attack due to a lack of awareness.
Until now, OT security training was very expensive and organizations could only train a few of their employees every year. However, now with the Abhisam OT cyber security awareness training course, you can train anybody that may need training, across the organiztion in OT cyber security at a very low cost per person. So you can deploy this training to not just your manufacturing staff, but also your IT staff. Organizations must take this opportunity to train as many people as possible in the basics of OT cyber security.
If you need a higher level course, then you can also consider enrolling some of your employees in the Abhisam Certified Industrial Cybersecurity Professional (CICP) course. This course is also much more cost effective than similar courses from other providers when you see the scope that it covers.

What does this OT cyber security awareness training course include?
This course has four modules as below:
1. Basic Concepts about different Industrial Operations and OT systems such as DCS, PLC, SCADA, SIS.
2. Basic Concepts about Cyber security, vulnerabilities in OT systems
3. Past attacks on ICS systems in industry.
4. Industry Standards & Practices (Introduction to IEC 62443 & NIST 800-82)
This is followed by an exam, on passing the learner earns a certificate and an electronic badge.
If you are completely new to the subject then you may read the basics below to familiarize yourself with the technologies.
What is OT security in cyber security?
OT is short for Operational Technology and are computer based systems that are connected to physical objects such as mechanical, electrical, electronic, pneumatic, hydraulic or similar equipment and are used to monitor and control these equipments. Common examples of OT systems are Industrial Control Systems (ICS) and Safety Instrumented Systems (SIS).
These ICS may be of different kinds including Distributed Control Systems (DCS), Programmable Logic Controllers (PLC) and Supervisory Control and Data Acquisition (SCADA). All of them are OT systems.
OT Systems and IT Systems- what’s the difference?
These OT systems are different from IT (short for Information Technology) systems, which are also computer based, but process only data and are not connected to any physical objects. Examples of IT systems are Banking Systems, Stock Market trading systems, Credit Card Processing systems and Enterprise Resource Planning (ERP) systems.
OT systems, including all ICS are cyber physical systems, unlike IT Systems.
What’s the difference between IT and OT security?
IT security is concerned about protecting IT systems from cyber attacks. This includes protecting data and information from being stolen by adversaries, damaged, destroyed or otherwise corrupted.
Since IT systems are not directly connected to any physical objects, an attack on an IT System may result only in theft of data, or loss of data, or financial loss, but never any physical consequences.
However, in the case of OT systems, an attack on an OT system may result in not only loss of data and/or theft of data, but also result in physical damage to equipment and assets, injuries to people and degradation and damage to the environment as well as disrupt industrial operations.
This is because many OT systems are used for controlling large manufacturing plants that may process huge amounts of flammable, toxic or explosive materials and any disruption to the OT system that controls the plant may result in unwanted physical consequences.
So the potential bad consequences of an IT system attack and an OT system attack are quite different.
Secondly the IT environment and OT environment are different. Most well maintained IT environments may be updated with patches regularly and also may be monitored intensively for intrusions by a dedicated security operations center, with probably full time employees who are responsible for IT system security.
On the other hand OT environments have a lot of legacy stuff that may not be possible to patch, or having obsolete ICS systems that are no longer supported. These ICS systems may not be included in an SOC and probably have no full time employees who are responsible for cyber security. The plant engineer or Instrument & Control Systems engineer may be the one who is responsible for many things and security is just one of them. Thirdly the methods, tools and processes for protecting IT systems from cyber threats are different from those used to protect OT systems. Lastly the level of OT security awareness in an organization may be much lesser than for IT security awareness in the same organization.
Hence the security risks for IT Systems and OT systems are different.
IT networks and OT networks/Industrial networks
OT networks, like those in Industrial systems are typically closer to the physical objects that they control, so they are basically shopfloor networks in a manufacturing plant. The IT network may be connected to the OT network at various points. In a well designed secure environment these points of interconnection would be via a DMZ or other well defended portions that have restriction devices such as firewalls or unidirectional gateways. However, this may not always be the case. Hence there is a chance that malware from the IT network may reach the OT network.
What is critical infrastructure?
Critical infrastructure refers to those systems that are critical to running a country. This includes power generation plants, the electrical grid, city water supply systems, sewage treatment systems, port cargo handling systems, railways and so on. Most of these have OT systems having hardware and software at their core and can be attacked by adversaries to cripple the country. Hence it is very necessary for any country to protect this critical infrastructure, by protecting these OT systems.



