As you may already be aware, a new critical remote code execution vulnerability (CVE-2021-44228) affecting Apache Log4j software library versions 2.0-beta9 to 2.14.1 has been discovered.
What is the Log4j vulnerability?
Log4j is used in many websites, consumer and enterprise services and applications—as well as in operational technology products, which includes even Industrial Control Systems such as DCS, SIS, PLC, SCADA, Process Historians and similar hosts and controllers. For example vulnerable products include LOGO! PLC programming tool, used to configure LOGO! PLCs from Siemens.
Log4j is open source software developed by the Apache Foundation and it is used widely in all these systems, to ironically, log security and performance information. An unauthenticated remote actor could exploit this vulnerability to take control of an affected system.
This vulnerability is also referred to as Log4shell
Is there a list of systems affected? Does my Industrial Control System cybersecurity get affected by this?
Since a large number of systems use Log4j, many of these have been affected. However some vendors of these systems have moved quickly to patch them and/or advise workarounds. Others are still evaluating the vulnerabililty and whether it does affect their systems or not. Since this is not a consumer product or a stand alone system, but rather a software component, it will take a lot of time for vendors, including Industrial Control System vendors to evaluate if any of their systems, or the components of these systems do use this software and if they do whether the vulnerability can affect their system.
This is a typical case of a supply chain security issue. See more on Supply chain cybersecurity here.
Is there any advisory from Industrial Control System vendors?
Siemens has issued an advisory regarding their systems. Click here to view. One of the Github repositories shows Schneider EcoStruxure related products.
Industrial IoT products and systems also affected by Log4j?
Yes, many of those are affected too. This is because the vulnerability can affect cloud services providers such as Amazon Web Services (AWS) and Azure. Many of these providers have rushed to apply patches and issue fixes. Siemens Mindsphere is also affected, but Siemens have issued an advisory that shows what to do.
What steps is CISA (US Cybersecurity and Infrastructure Security Agency) taking?
CISA has created a webpage, Apache Log4j Vulnerability Guidance and will actively maintain a community-sourced GitHub repository of publicly available information and vendor-supplied advisories regarding the Log4j vulnerability. CISA will continually update both the webpage and the GitHub repository.
Take a look at this list which seems better formatted and arranged in alphabetical order of vendors.
https://github.com/NCSC-NL/log4shell/blob/main/software/README.md
A glance at the Github repository shows listing of many products from companies such as CISCO, Juniper networks and . This means that if these products are used in any Operational Technology systems, this could become an OT Security problem.
What are Operational Technology Systems?
Operational Technology systems are computer based systems that are used to monitor, control and operate real time control systems such as those used in industrial plants and facilities, transportation services (such as railways and ships), buildings and more. They include systems such as Distributed Control Systems (DCS), Programmable Logic Controllers (PLC), Supervisory Control and Data Acquisition Systems (SCADA), Safety Instrumented Systems (SIS), Building Management Systems (BMS) and similar.
OT systems cybersecurity is a different ball game altogether. Read here to know the differences between OT Security and plain vanilla business IT security.
What is Industrial Cybersecurity?
Industrial Cybersecurity refers to the cybersecurity of Industrial Control Systems such as the DCS, PLC, SCADA, SIS and BMS systems mentioned earlier. The steps to secure these systems, as well the implications of an attack on these systems is completely different from attacks on IT systems. This is because Industrial Cybersecurity related events can cause plants to stop running, or worse, lead to accidents such as loss of containment of hazardous materials, or explosions and fires. In case of systems that control transportation, such as ships, it may mean loss of control of steering or navigation systems, leading to disastrous accidents. Read more here.
What can Asset Owners and those who are responsible for ICS Security do?
CISA urges organizations to review its Apache Log4j Vulnerability Guidance webpage and upgrade to Log4j version 2.15.0, or apply the appropriate vendor recommended mitigations immediately. CISA will continue to update the webpage as additional information becomes available.
If you have an Asset Inventory of your Industrial Control System, then you can contact your vendor to ask about how the Log4j vulnerability affects their system. You may not get an immediate answer, because they may need time to evaluate their own supply chain to find out. If any patches have been released, then you can start implementing Patch Management or apply any suggested workarounds.
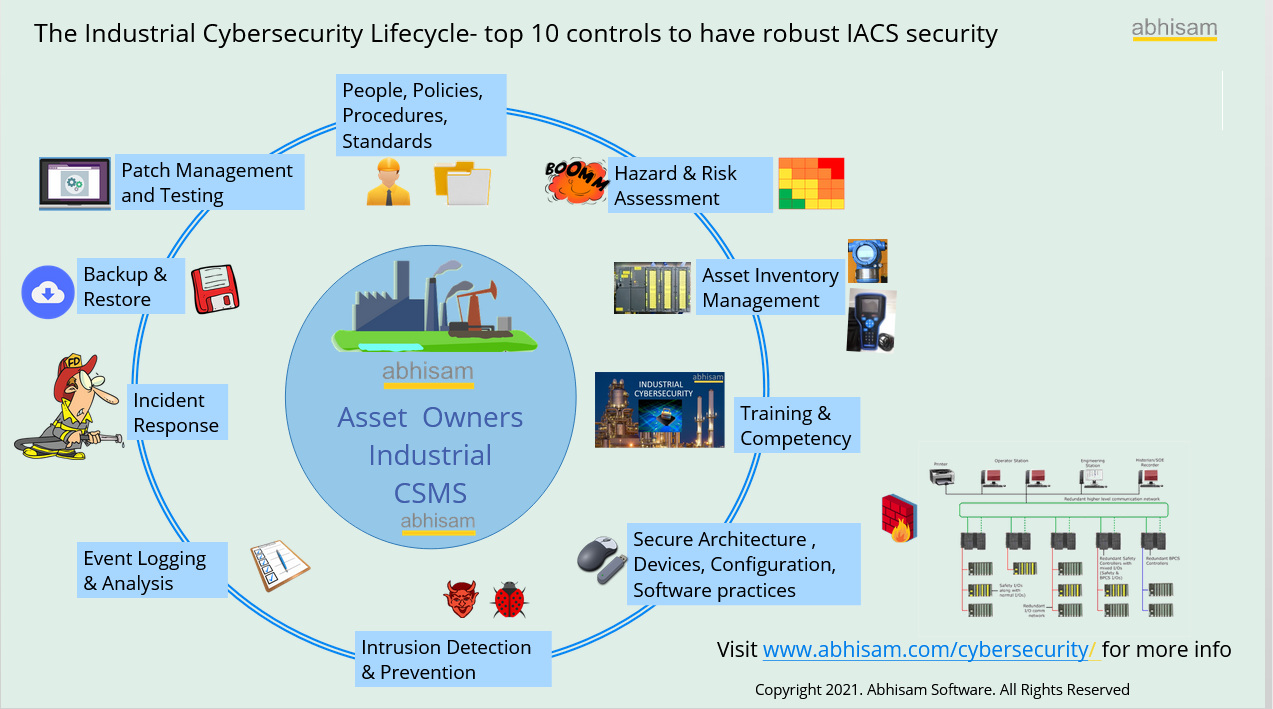
If you have followed the Abhisam Industrial Cybersecurity course, that leads to the CICP certification, then you may be already aware of all this.
Refer to the Abhisam Industrial Cybersecurity lifecycle to understand things better. Click the chart below to see an interactive version.
Software Bill of Materials (SBOM)
If you have carried out any SBOM exercise on your systems, then you can easily find out if your list has the log4j library. SBOM is short for software bill of materials and refers to the detailed listing and breakdown of what components are present in the software that is used. Most industrial and commercial software use several different software packages and components, not everything is programmed from scratch. Hence this SBOM helps you find out which software components are present in your system. If a vulnerability in one of them is discovered, you can quickly refer to this SBOM and find out if you are using that component or not. This will immediately indicate what action you need to take, or not.